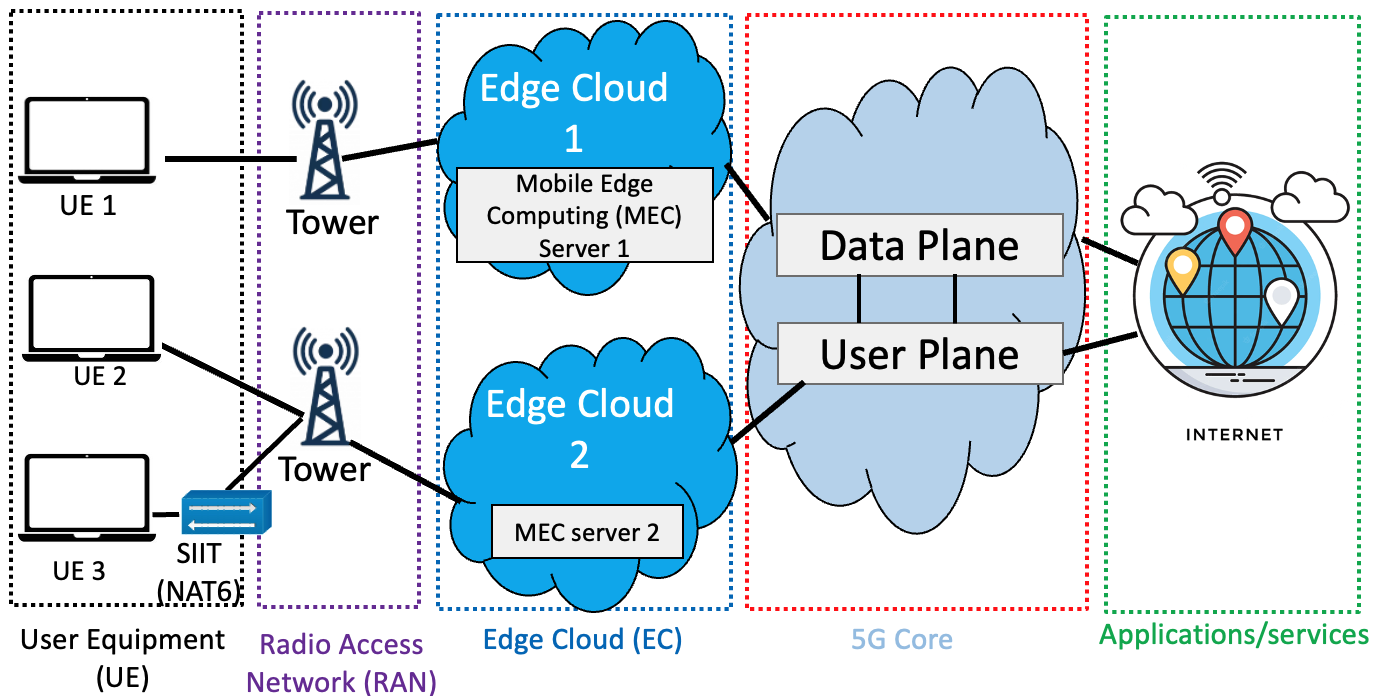
The testbed for the WUSTL-HDRL-2024 dataset was developed with a focus on simulating a dynamic 5G network environment, aiming to address the gap in datasets that encompass a wide range of 5G network interactions and security threats [1].
The 5G Security Testbed is segmented into six components: a 5G Core, a Local Network, Multi-access Edge Computing (MEC) servers, User Equipment (UE), an Insider Attacker, and a Routing system. The data flow begins with the 5G Core, where an Ubuntu 20.04 computer uses Simu5G to mimic 5G network operations, extending its capabilities to include multiple MECs and external hosts. From the 5G Core, the data is processed through the Local Network, incorporating Stateful IP/ICMP Translation (SIIT) to bridge IPv6 and IPv4 communications, addressing compatibility issues within the simulated 5G network. MEC servers, vital for processing edge computing tasks, monitor network traffic and host data for intrusion detection. User Equipments (UEs), varying in operating systems, connect directly to the 5G network or through the Local Network, depicting a variety of end-user scenarios. An Insider Attacker machine is configured to execute a series of attacks, testing the network's defense mechanisms. Lastly, a central Router oversees the testbed's data management, ensuring the generation of a diverse and unpredictable attack dataset for robust security analysis.

The dataset includes four types of security breaches: Man-in-the-Middle (MiTM) attacks, Distributed Denial of Service (DDoS) attacks, Ransomware, and Buffer Overflow attacks. MiTM attacks involve altering or intercepting data between UEs and MECs, threatening data confidentiality and integrity. DDoS attacks flood the MECs with excessive requests, disrupting service. Ransomware encrypts critical files, demanding payment for access, while Buffer Overflow attacks exploit software vulnerabilities to execute unauthorized code.
Network interactions and attack instances were captured and cataloged in a "CSV" file using Audit Record Generation and Utilization System (ARGUS) network monitoring tool [2]. This dataset provides a comprehensive overview of network security threats in a 5G context, featuring a mix of network flow metrics, host metrics, and attack patterns, labeled based on the source of the threat for precise identification and analysis.
| Measurement | Value |
|---|---|
| Dataset size | 81.7 MB |
| Number of normal samples | 132k (91%) |
| Number of attack samples | 13k (9%) |
| Total number of samples | 145k |
Download the WUSTL-HDRL-2024 dataset from HERE (81,675,964 bytes)
Acknowledgment: This work has been supported in part by Prince Sattam Bin Abdulaziz University, AlKharj, Saudi Arabia. The statements made herein are solely the responsibility of the authors.
References: