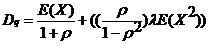
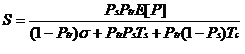

| Meaning | Value (802.16) |
| Number of SS | 20 |
| Preamble (Beacon) | 3 us |
| Each MAP | 5 us |
| Downlink DATA | 8 us |
| Register Contention | 1 us |
| Contention Period | Number of active stations |
| Average data packet size | Each traffic 100~200 bytes |
| Fixed Frame size | 1 ms |
| PHY rate | 50 Mbps |