Survivability in IP over WDM networks
Kulathumani Vinodkrishnan, Nikhil Chandhok, Arjan Durresi, Raj Jain1,
Ramesh Jagannathan, and Srinivasan Seetharaman
Department of Computer and Information Science, The Ohio State University,
2015 Neil Ave, Columbus, OH 43210-1277
Phone: 614-688-5610, Fax: 614-292-2911,
Email:
{vinodkri, chandhok, durresi, rjaganna, seethara}@cse.wustl.edu
1Chief Technology Officer, Nayna Networks, Inc., 157 Topaz St, Milpitas, CA 95035,
Phone: 408-956-8000X309, Fax: 408-956-8730 Email: raj@nayna.com
Abstract
The Internet is emerging as the new universal telecommunication medium. IP over WDM has been envisioned as one of the most attractive architectures for the new Internet. Consequently survivability is a crucial concern in designing IP over WDM networks. This paper presents a survey of the survivability mechanisms for IP over WDM networks and thus is intended to provide a summary of what has been done in this area and help further research. A number of optical layer protection techniques have been discussed. They are examined from the point of view of cost, complexity, and application. Survivability techniques are being made available at multiple layers of the network. This paper also studies the recovery features of each network layer and explains the impact of interaction between layers on survivability. The advantages and issues of multi-layer survivability have been identified. The main idea is that the optical layer can provide fast protection while the higher layers can provide intelligent restoration. With this idea in mind, a new scheme of carrying IP over WDM using MPLS or Multi Protocol Lambda-Switching has been discussed. Finally, an architecture is suggested by means of which the optical layer can perform an automatic protection switch, with priority considerations with the help of signaling from the higher layers.
Introduction
Challenges presented by the exponential growth of the Internet have resulted in the intense demand for broadband services. In satisfying the increasing demand for bandwidth, optical networks and more precisely WDM technologies represent a unique opportunity for their almost unlimited potential bandwidth [14, 15]. On the other hand, practically all end-user communication applications today make use of TCP/IP, and it has become clear that IP is going to be the common traffic convergence layer in communication networks. Consequently IP over WDM has been envisioned as the winning combination of the new network architecture [2].
At present, WDM is mostly deployed point-to-point and the current approaches consist of a multi-layered architecture comprising top most IP/MPLS layer over ATM over SONET/SDH over WDM as shown in Figure 1. An appropriate interface is designed to provide access to the WDM network. Multiple higher layer protocols can request light paths to peers connected across the optical network. This architecture has four management layers. One can also use a packet over SONET approach, doing away with the ATM layer, by putting IP/PPP/HDLC into SONET/SDH framing. This architecture has three management layers. The most attractive proposal is the two-layer model, which aims at a tighter integration between IP and optical layers, and offers a series of important advantages over the current multi-layer architecture. The benefits include more flexibility in handling higher capacity networks, better network scalability, more efficient operations and better traffic engineering. MPLS is proposed as the integrating structure between IP and optical layers. MPLS brings two main advantages. First it can be used as a powerful instrument for traffic engineering and second it fits naturally with WDM when labels are wavelengths. An extension of the MPLS has been proposed for IP/WDM integration. This is called the Multi-protocol lambda switching which equates wavelengths to labels [3].
With the introduction of IP in telecommunications networks, there is tremendous focus on reliability and availability of the new IP-WDM hybrid infrastructures. Automated establishment and restoration of end to end paths in such networks require standardized signaling and routing mechanisms. As a result network survivability is a major criteria in comparing the solutions for integrating IP over WDM as well as the main factor in designing and operating these networks. There are several proposals stating that the optical layer itself should provide restoration/protection capabilities of some form. This requires careful coordination with the mechanisms of the higher layers such as the SONET APS and the IP re-routing strategies. Hold-off timers have been proposed to inhibit higher layers backup mechanisms. Problems can also arise from the high level of multiplexing. The optical fiber links contain a large number of higher layer flows such as SONET / SDH, IP flows or ATM VCs. Since these have their own mechanisms, a flooding of alarm messages can take place. A better integration between IP and optical will provide opportunities to implement a better fault restoration [9].
Survivability refers to the ability of a network to maintain an acceptable level of service during a network or equipment failure. Mechanisms for survivability can be built at the optical transport layer or at higher network layers such as IP or ATM. The physical layer is 'close' to most of the usual faults that occur, such as a cable cut. Survivability mechanisms in the optical layer involve detecting this and performing a simple switch to divert the traffic through an alternate path. This is called protection [12]. Optical layer mechanisms are inherently faster than higher layer mechanisms. Various protection mechanisms are examined from a cost and services point of view in Section 1 of this paper.
Considerations for higher layer survivability are discussed in Section 2. At a higher layer, an alternate path can be worked out on the basis of an algorithm, priority considerations can be made and the process can be more intelligent. This is called restoration of traffic and is more time consuming than protection [13]. Hence, this mechanism cannot be used alone. It has to work along with the optical layer protection.
Section 3 concentrates on IP over WDM integration using MPLS and the way that this architecture can handle survivability. The advantages of such architecture are also examined in that section. Section 4 hints at a new method by which the higher layer, i.e MPLS can configure the opto-mechanical switches at the optical layer to automatically switch only certain priority traffic. This would combine the advantages of intelligence and speed. This architecture and associated problems are discussed in section 4.
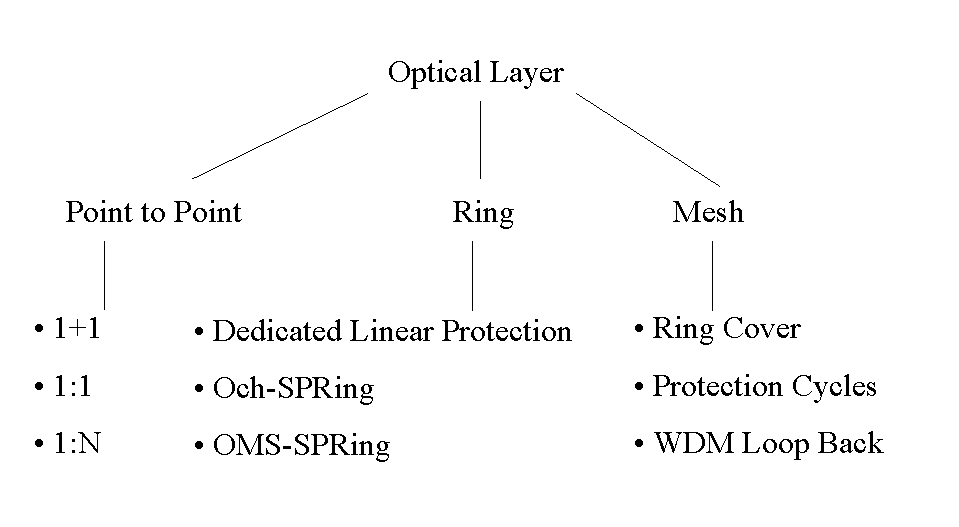
1. Optical layer protection
Optical transport networking (OTN) is a major step in the evolution of transport networking. From an architectural point of view, the OTN is very similar to SONET/SDH. However, the major differences arise from the multiplexing technology. It is digital TDM for SDH and analog WDM for OTN. The complexities associated with analog network engineering and maintenance implications account for the majority of the challenges associated with OTN.
Survivability is central to optical networking's role as the unifying transport architecture. Survivability mechanisms at this layer are very similar those of SONET/SDH and can offer the fastest possible recovery from fiber cuts and other physical media faults. The telecommunication industry has traditionally required a recovery time in the order of 50 ms.
The optical layer can be sub-divided into 2 parts, the optical channel and the optical multiplex section [1]. The optical channel corresponds to each wavelength that is being carried across the OTN. The optical multiplex section is the collection of wavelengths that arrive at an optical add/drop multiplexer in the network. Providing survivability at the channel level would be a very flexible option. By doing this, protection bandwidth can be reserved only for certain high priority channels and bring about higher efficiency.
Three different kinds of topologies are possible: point to point, ring, and arbitrary mesh as illustrated in Figure 2. These topologies are discussed next.
1.1. Point-to-Point Mechanisms
In case of point to point, one can provide 1+1, 1:1 or 1:N protection. In 1+1, the same information is sent through 2 paths and the better one is selected at the receiver. The receiver makes a blind switch when the selected (working) paths signal is poor. Unlike SONET, a continuous comparison of 2 signals is not done in the optical layer. Switching can be done as soon as light is not detected at the current signal port. The splitting of the signals is done usually after conversion into optical signals by the transponder, otherwise even the transponders would have to be twice in number.
In 1:1 protection, signal is sent only on the working path while a protection path is also set but it can be used for lower priority signals that are preempted if the working path fails. A signaling channel is required to inform the transmitter to switch path if the receiver detects a failure in the working path. A generalization of 1:1 protection is 1:N protection in which one protection fiber is shared among N working fibers. It is usually applied for equipment protection [8].
1.2. Ring systems
Ring mechanisms are broadly classified into: Dedicated linear protection and Shared protection rings [10].
Dedicated linear protection is an extension of 1+1 protection applied to a ring and is illustrated in Figure 3. It is effectively a path protection mechanism. Entire path from source to the destination node is protected. Since each channel constitutes a separate path, it is also called Optical Channel Subnetwork Connection Protection (OCh-SNCP). From each node, the working and protection signals are transmitted in opposite directions along the 2 fibers. At the receiving end, if the working path signal is weak, the receiver switches to the protection path signal. For example, consider the path between the OADM 2 and OADM 1 in Figure 3. The signal is sent on two paths: B-A and B-C-D-A. OADM 1 receives the signal on both paths but selects the stronger signal, say, B-C-D-A. This is the working path, denoted as W. When the link C-D fails, OADM 1 starts taking input from the protection link between B and A. The Path selector is the circuit that selects the stronger signal. The bridge is a switch that transmits the same traffic on both of its connections. The bridge at B transmits the traffic along BA and BC.
Each channel or path can be added or dropped at any pair of nodes. Thus multicasting can be easily supported. Hence, this is usually applied to hubbed transport scenarios. For other types of connections, it is very expensive [5]. There is heavy loss due to the splitters and the entire bandwidth is wasted on the protection fibers.
Shared protection rings (SPRings) protect a link rather than a path. Hence, they are easier to setup and are the more common ring protection mechanisms. Figure 4 shows a 2-fiber SPRings case with two counter-rotating rings. Half the wavelengths in each fiber are reserved for protection. If a link failure occurs, the OADM adjacent to the link failure bridges its outgoing channels in a direction opposite to that of the failure and selects its incoming working channels from the incoming protection channels in the direction away from the failure. For example, in Figure 4, C-to-A signal traverses the inner ring along A-B-C, while A-to-C signal traverses on the outer ring along the path C-A-B. If the outer ring link between A and B fails, working traffic between A and C will now take the path A-D-C-B-C. Note that the transmission from A has been switched from the inner ring to outer ring. This is called ring switching. The problem with this is the long length of the protection paths, which may limit its use to short haul metropolitan networks.
Figure 5 shows the 4-fiber SPRings case. Two fibers each are allocated for working and protection. The operation is similar to that of the 2-fiber SPRing. However, this system can allow span switching in addition to ring switching. Span switching means that if only the working fiber in a link fails, the traffic can use the protection fiber in the same span. In case of 2-fiber systems, it will have to take the longer path around the ring. In the figure, if the working link between A and B fails, the traffic between A and C will still take the shorter path, A-B-C.
Sometimes the need arises to protect against isolated optoelectronic failures that will affect only a single optical channel at a time. Thus, a protection architecture that performs channel level switching based on channel level indications is required. The Optical Multiplexed Section (OMS) SPRings, discussed so far, switch a group of channels within the fiber. The Optical Channel (OCh) SPRings are capable of protecting OChs independent of one another based on OCh level failure indication. An N-Channel OADM based 4-fiber ring can support upto N independent OCh SPRings. Such architectures are also called Bi-directional wavelength path switched ring architectures (BWPSR)
SPRing architectures are referred to as Bidirectional line switched ring (BLSR) architectures. OCh SPRings are referred to as Bidirectional Wavelength Line Switched Ring technology, (BWLSR). ITU-T draft recommendation G.872 describes a transoceanic switching protocol for 4-fiber OMS SPRings. This protocol requires that after a span switching a path should not traverse any span more than once. When ring switching occurs, this may not be true. This protocol is essential in long-distance undersea transmissions to avoid unnecessary delay. A Summary of point-to-point and ring architectures is shown in Table 1.
1.3. Mesh Architectures
Along a single fiber, any two connections cannot use the same wavelength. The whole problem of routing in a WDM network with proper allocation of a minimum number of wavelengths is called the routing and wavelength assignment (RWA) problem. It is found that in arbitrary mesh architectures, where the connectivity of each node is high, the number of wavelengths required greatly decreases. This is the advantage of having a mesh architecture. Moreover addition of new nodes and removing existing nodes becomes very easy. There are 3 broad methods for using mesh architectures. These are as follows:
To perform alternate route computation after failure occurs:
This itself can be brought about in the following ways: Having a centralized route computer would mean route flexibility but a single point of failure. Distributed processing can be brought about by performing rote computation at the ends of failed line or the end of the path, but route flexibility is compromised. There is lot of signaling complexity associated with this method.
To have pre-computed routing tables:
With this method, either a 1+1 path protection (protection routes are dedicated to a given working route) or a fully flexible protection route (depending on the failed resource and the affected light path) can be used. The latter is bandwidth efficient but comes with additional size and complexity of the protection tables to be maintained.
Using automated protection switching:
Both the above methods are time consuming. Hence, an automatic protection switching mechanism, like that for the rings, is required. Three alternatives are briefly discussed here:
1.3.1 Ring Covers
The whole mesh configuration is divided into smaller cycles in such a way that each edge comes under atleast one cycle. Along each cycle, a protection fiber is laid. It may so happen that certain edges come under more than one cycle. In these edges, more than one protection fiber will have to be laid. Hence, the idea is to divide the graph into cycles in such a way that this redundancy is minimized [16]. However, in most cases the redundancy required is more than 100%.
1.3.2 Protection Cycles
This method reduces the redundancy to exactly 100%. The networks considered have a pair of bi-directional working and protection fibers. Fault protection against link failures is possible in all networks that are modeled by 2-edge connected digraphs. The idea is to find a family of directed cycles so that all protection fibers are used exactly once and in any directed cycle a pair of protection fibers is not used in both directions unless they belong to a bridge[4].
For planar graphs, such directed cycles are along the faces of the graph. For non-planar graphs, the directed cycles are taken along the orientable cycle double covers, which are conjectured to exist for every digraph. Heuristic algorithms exist for obtaining cyclic double covers for every non-planar graph.
The maximum number of failures that such an architecture can protect with exactly 100% redundancy, given that no two failures occur in the same protection cycle, is F/2 rounded to the lower integer, where F is the number of faces for the planar graph. For a non-planar graph, the number is (n-1)/2 where 'n' is the order of the graph[4].
Figure 6 shows five protection cycles formed along the faces of a planar graph. The two directions of link 'a' are protected by cycles 1 and 2. The right to left direction of traffic along link a would be directed along protection cycle 1 and the left to right direction of traffic would now reach its destination along cycle 2. Thus both directions of traffic are protected. Similarly, the 2 directions of link 'b' are protected by cycles 3 and 5.
1.3.3 WDM Loop back recovery
A double-cycle ring cover covers a graph such that each edge is covered by two cycles. Cycles can then be used as rings to perform restoration. For a two edge connected planar graphs, a polynomial time algorithm exists which can create double-cycle covers. For two-edge connected non-planar graph, the existence of a double-cycle cover is a conjecture and no algorithm other than an exhaustive search exists[11].
Primary and secondary wavelengths cannot be assigned in such a way that a wavelength is secondary or primary over a whole ring. Therefore, the cycle double cover requires wavelength changers which are costly or infeasible.
General method of selecting directions and Performing WDM Loop-back for link failures
An undirected graph G = (N, E) is a set of nodes N and edges E. With each edge [x,y] of an undirected graph, arcs (x, y) and (y, x) are associated. A directed graph P = (N, A) is a set of nodes N and directed arcs A. Given a set of directed arc A, define the reversal of A to be A = { (i, j) | (j, i) e A}. Similarly, given any directed graph P = (N, A) define P = (N, A) to be the reversal of P.
A graph G = (N, E ) is called "two-vertex (edge)-connected" if removal of any one vertex leaves the graph connected. The idea is to create a pair of spanning sub-graphs, B = (N, A) and R = B = (N, A) each of which can be used for primary connections between any pair of nodes in the graph. In the event of a failure, connections on one wavelength in B are looped back on the same wavelength around the failure using R. In figure 7, two spanning tress B and R have been shown for the graph G
Consider the example shown in Figure 7. If [y, z] were to go down , then all the traffic going from y to z would use the graph R and go from y -> x -> w -> z . Then z will use graph B itself to route the traffic as it would do if the traffic would have arrived from x. Now for traffic coming from z to y, B is used and traffic is routed z-> w -> x -> y. Edge [y, z] can be successfully bypassed if there exists a path with sufficient capacity from y to z in R and a path with sufficient capacity exists from z to y in B. Details of determining B, given a graph G can be found in [6].
Advantages of WDM Loop back recovery are that it:
2. Consideration for Multi-layer survivability
The optical layer forms the lowest layer of the network architecture. It provides the service of transport to higher layers. The issues are choice of the higher layers and the presence of survivability mechanisms in one or more of the higher layers. Following problems are encountered if only the optical layer provides survivability:
However, there exist complications with multi-layer survivability.
Multi-layer recovery can combine the merits of optical layer and the higher layer schemes. More specifically, the protection mechanism of optical layer can be combined with the restoration mechanism of the higher layers. A good strategy would be the nesting of survivability mechanisms and avoidance of unnecessary interworking.
The rerouting capability of the optical layer can be expanded and newer bandwidth efficient protection can be facilitated if there is some controlled coordination between the optical layer and a higher layer that has a signaling mechanism. Similarly, the optical layer which cannot detect faults in the router or switching node, could learn of the faults if the higher layer communicated this to it. Then, the optical layer can initiate protection at the lower layer.
Fast signaling is the main advantage of the MPLS layer in protection. Since MPLS binds packets to a route (or path) via the labels, it is imperative that MPLS be able to provide protection and restoration of traffic. In fact, a protection priority could be used as a differentiating mechanism for premium services that require high reliability. The MPLS layer has visibility into the lower layer, which alerts about faults by a liveness signaling message. The IP/MPLS over WDM architecture seals off SONET APS protection from the discussion and the WDM optical layer provides the same kind of restoration capabilities at the lower layer. Thus there has to be interaction only between the MPLS and optical layer, with no unwarranted intervention from the SONET layer. This restoration mechanism and how it can operate with optical layer protection are discussed in the next section.
3. Survivability in IP over WDM using MPLS architecture
The model consists of IP routers attached to an optical core network. The optical network consists of multiple Optical Cross-Connects (OXCs), interconnected by optical links. Each OXC is capable of switching a data stream using a switching function, controlled by appropriately configuring a cross- connect table [9]. The switching within the OXC can be accomplished either in the electrical domain, or in the optical domain. In this network model, a switched optical path is established between IP routers[3].
In Multiprotocol Label Switching (MPLS), a label added to the packet is used for forwarding decisions at each hop. The path specified by the labels is called a Label Switched Path (LSP). Each LSP has a set of criteria associated with it, which describes the traffic that traverses the LSP. The set of criteria groups the traffic into Forwarding Equivalence Classes (FECs). FECs associate IP traffic with what is commonly called a next hop: a tuple that defines the interface and the low level IP address of the next IP router. LSPs are setup using signaling protocols like Resource Reservation Protocol (RSVP) or Constraint-based Label Distribution Protocol (CR-LDP). A device that can group traffic into an FEC is called a Label edge router. Other routers along the path simply use labels and are called "Label Switched Routers" or LSR. An LSR performs label switching by establishing a relation between an <input port, input label> tuple and an <output port, output label> tuple. Similarly, OXC provisions optical channel trail by establishing a relation between an <input port, input optical channel> tuple and an <output port, output optical channel> tuple. An arbitrary mesh connection of optical routers (OXCs) is shown in Figure 8.
Protection switching relies on rapid notification of failures. Once a failure is detected, the node that detected the failure must send out a notification of the failure by transmitting a Failure Indication Signal (FIS) to those of its upstream LSRs that were sending traffic on the working path that is affected by the failure. This notification is relayed hop-by-hop by each subsequent LSR to its upstream neighbor, until it eventually reaches a Path Switched LSR, (PSL). The PSL is the LSR that originates both the working and protection paths, and the LSR that is the termination point of both the FIS and the FRS. Note that the PSL need not be the origin of the working LSP.
The Path Merge LSR (PML) is the LSR that terminates both the working path and its corresponding protection path. Depending on whether or not the PML is a destination, it may either pass the traffic on to the higher layers or may merge the incoming traffic on to a single outgoing LSR. Thus, the PML need not be the destination of the working LSP. An LSR that is neither a PSL nor a PML is called an intermediate LSR. The intermediate LSR could be either on the working or the protection path, and could be a merging LSR (without being a PML).
Since the LSPs are unidirectional entities and protection requires the notification of failures, the failure indication and the failure recovery notification both need to travel along a reverse path of the working path from the point of failure back to the PSL(s). When label merging occurs, the working paths converge to form a multipoint-to-point tree, with the PSLs as the leaves and the PML as the root. The reverse notification tree is a point-multipoint tree rooted at the PML along which the FIS and the FRS travel, and which is an exact mirror image of the converged working paths
The establishment of the protection path requires identification of the Working path, and hence the protection domain. In most cases, the working path and its corresponding protection path would be specified via administrative configuration, and would be established between the two nodes at the boundaries of the protection domain (the PSL and PML) via explicit (or source) routing using LDP, RSVP, signaling (alternatively, using manual configuration).
The Reverse Notification Tree (RNT) is used for propagating the failure indication and restoration signals and can be created very easily by a simple extension to the LSP setup process as shown in Figure 9. During the establishment of the working path, the signaling message carries with it the identity (address) of the upstream node that sent it. Each LSR along the path simply remembers the identity of its immediately prior upstream neighbor on each incoming link. The node then creates an inverse cross-connect table that for each protected outgoing LSP maintains a list of the incoming LSPs that merge into that outgoing LSP, together with the identity of the upstream node that each incoming LSP comes from. Upon receiving an failure indication signal the LSR does the following:
The reverse notification tree arising from node 8 is shown in the figure 9. When the link between 5 and 8 fails, the failure indication signal starts from 5. At node 4, it will branch to 6 and 3. [7].
The advantages of the above architecture are:
So far, we have seen the different existing methods to provide survivability in an optical network. Each method has its own advantages and complexities. This section hints at a method of combining the good features of all.
Consider the overlay network configuration shown in Figure 10. Light paths need to be established through the various optical switches in the optical subnet for end-to-end transfers between the edge switches. The edge switches are those where the optical signal is first introduced. The optical subnet is assumed to be a mesh architecture considering its inherent advantages.
Each light path (connection) may have different setup, hold, and restore priorities, say from 1 to 3. At the time of connection setup, the requests with high setup priorities are allocated resources first. Hold priority determines the eligibility of a connection to be preempted if a shortage of resources arises. Connections with low hold priority are preempted if a high priority request needs resources for initial setup or restoration. The restoration priority determines the order in which the connections are restored upon a failure. Connections with high restoration priority may have protection paths setup while those with lowest restoration priority may not be restored at all. Although connections with high setup priority may also have high hold priority and a high restoration priority, these three priorities could be different.
In case of a failure along a high restoration priority light path, it would just mean a mechanical switch to the already configured alternate path, when there is available bandwidth along the alternate path. Otherwise, there is a slight signaling complexity involved, that being to preempt the existing low priority traffic and then switch. The signaling complexity can be avoided, if extra bandwidth is reserved for very high priority traffic. The switching is fast in this case, as it is done on the basis of wavelength and no "thinking" is involved. Such switches exist in BWPSR or Bi-directional wavelength path switched ring architecture, where switching is done on a wavelength basis, but for a ring architecture. This is an extension to the mesh architecture.
Figure 10 shows various edge switches interconnected through an optical subnet. Various paths of different setup, hold and restoration priorities exist through the network. The high restoration priority path 1-2-3 can be switched through 1-4-3 if the links 1-4 and 4-3 have additional reserved capacity. Otherwise, preemption signals would have to be sent to the neighboring nodes before performing the switch.
This method is a trade-off between signaling time and bandwidth efficiency, based on traffic priority.
As seen in the previous section, the general architecture for the optical layer will be a mesh structure of optical switches. The routers at the edge of these networks will receive Ip packets and will try to route them through the optical network. Further work needs to be done to find the optimal working and protection paths to route these packets. Classes of service need to be implemented, based on protection requirements. The idle protection paths should be utilized as working paths of low priority traffic. Thus, given a source, destination, requested bandwidth and the protection priority, the problem is to find a pair of optimal paths. If it is a low priority traffic, the goal is to find just one path, which could be the idle protection path of some other working path. Signals to preempt the low priority traffic also need to be implemented.
Various survivability techniques at the optical layer of IP over WDM architecture were presented. These were essentially Automatic Protection Switching (APS) mechanisms. They are fast with a switching time of the order of 50 ms. Multi-layer survivability adds intelligence into the process and establishes a fine grain of control by setting up priorities and bringing quality of service into survivability. Reliance on SONET in WDM systems inhibits growth of packet over fiber technology. Restoration mechanisms at the IP layer are extremely slow. Hence, IP over WDM using lambda switching is being considered. This offers restoration through fast signaling. Priorities can be added. Inter working with the WDM layer can be regulated using timers. Finally, a method is then suggested in which signaling is used to configure protection paths in the optical layer and perform a fast protection switch for high priority traffic. This makes the optical layer itself very intelligent.
References
[1] ITU-T, Architecture of Optical Transport Networks, Draft Rec. G.872, Feb. 1999, SG 13.
[2] P. Bonenfant, A. Rodriguez-Moral, J. Manchester, "IP over WDM: The Missing Link ", white paper, Lucent Technologies, 1999.
[3] N. Chandhok, A. Durresi, R. Jagannathan, R. Jain, S. Seetharaman, and K. Vinodkrishnan, "IP over Optical Networks: A Summary of Issues," IETF draft, March 2000.
[4] G. N. Ellinas, "Fault Restoration in Optical Networks: General Methodology and Implementation", PhD thesis, Columbia University.
[5] O. Gerstel and R. Ramaswami, "Optical layer survivability: A Services Perspective", IEEE Communications, March 2000, pp.104 113.
[6] N. Ghani ," Lambda Labelling: A Framework for IP-Over-WDM Using MPLS", Optical Networks Magazine, April 2000, pp 45-57.
[7] C. Huang, V. Sharma, S. Makam, and K. Owens, "A Path Protection/Restoration Mechanism for MPLS Networks", IETF draft, draft-chang-mpls-path-protection-00.txt , March 2000.
[8] D. Johnson, N. Hayman and P. Veitch, "The Evolution of a Reliable Transport Network", IEEE Communications , August 1999, pp. 52-57.
[9] J. Luciani, B. Rajagopalan, D. Awduche, B. Cain, B, Jamoussi, "IP over Optical Networks - A Framework", Internet Draft, draft-ip-optical-framework-00.txt, Mar 2000
[10] J. Manchester, P. Bonenfant and C. Newton, "The Evolution of Transport Network Survivability," IEEE Communications, August 1999, pp. 44-51.
[11] M. Medard, S. G. Finn, R. A. Barry, "WDM Loop-back Recovery in Mesh Networks" , in Proc OFC 98 pp. 298-299.
[12] S. Ramamurthy, B. Mukherjee, "Survivable WDM Mesh Networks, Part I Protection" , in: Proc. IEEE Infocom 99, Vol. 2, pp 744-751.
[13] S. Ramamurthy, B. Mukherjee, "Survivable WDM Mesh Networks, Part II Restoration", in: Proc. ICC99, Vol. 3, pp 2023-2030.
[14] R. Ramaswami and K. Sivarajan, "Optical Networks: A practical Perspective", Morgan Kaufmann, San Francisco, 1998.
[15] T. E. Stern, K. Bala, "Multiwavelength Optical Networks: A Layered Approach", Addison-Wesley, 1999.
[16] T.H. Wu, A Passive Protected Self Healing Mesh Network Architecture and Applications, IEEE Transactions on Networking, Vol. 2, No. 1, February 1994.

Figure 2: Classification of protection mechanisms
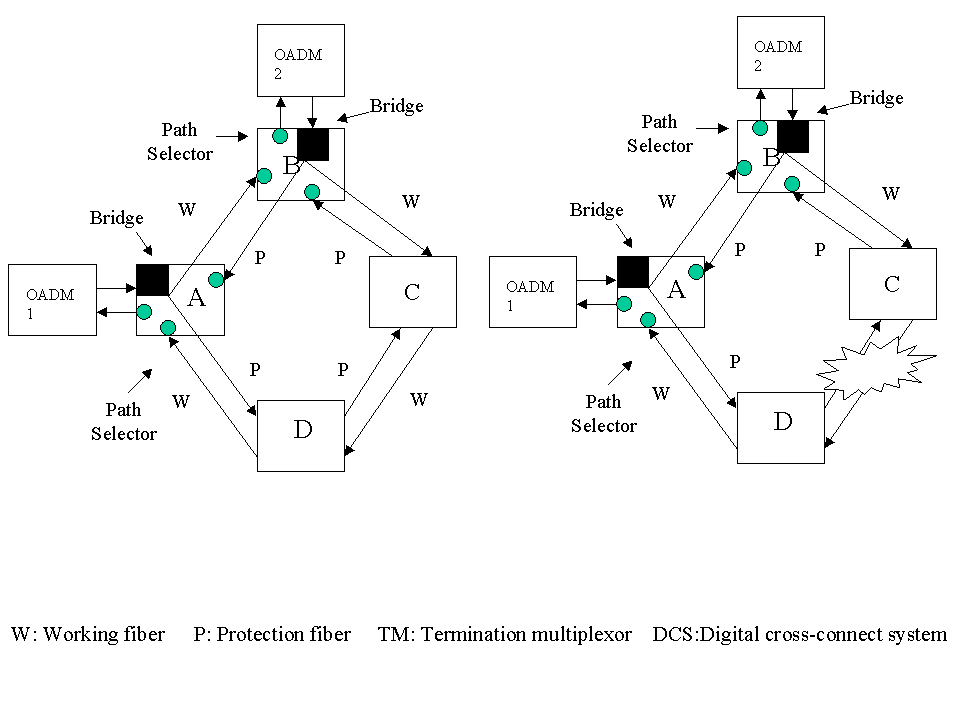
Figure 3: Dedicated Linear Protection
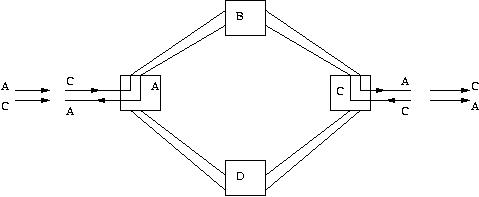
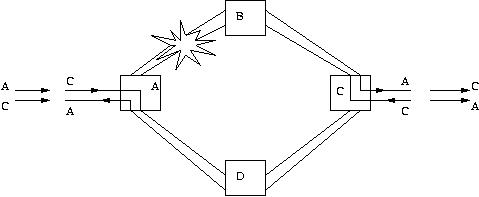
Figure 4. Two Fiber SPRing - Showing Ring Switching
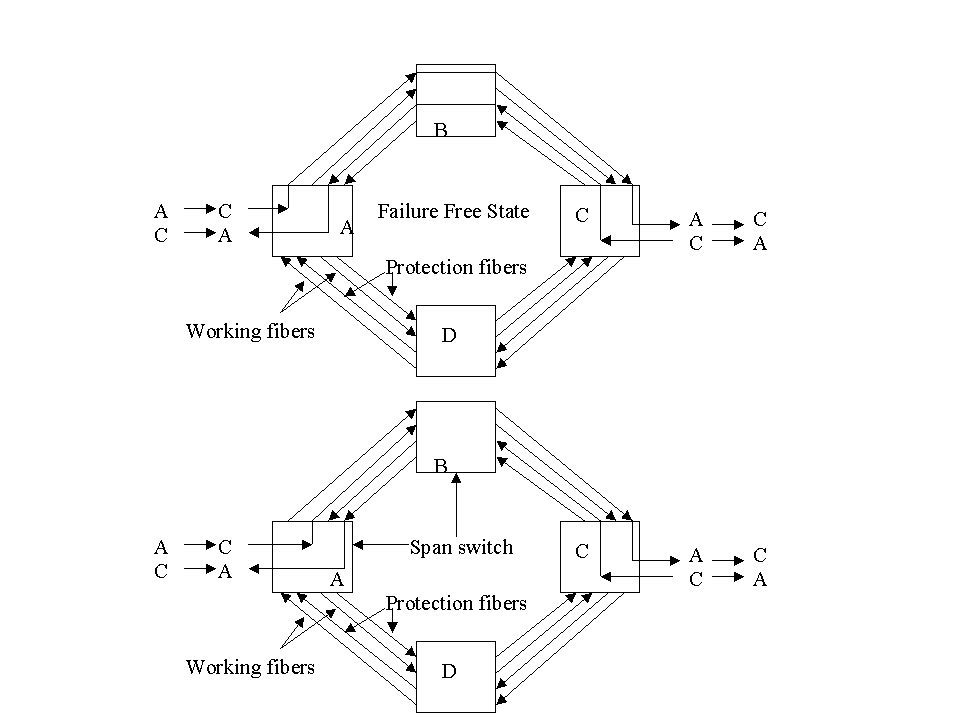
Figure 5. 4 fiber SPRing - Showing Span Switching
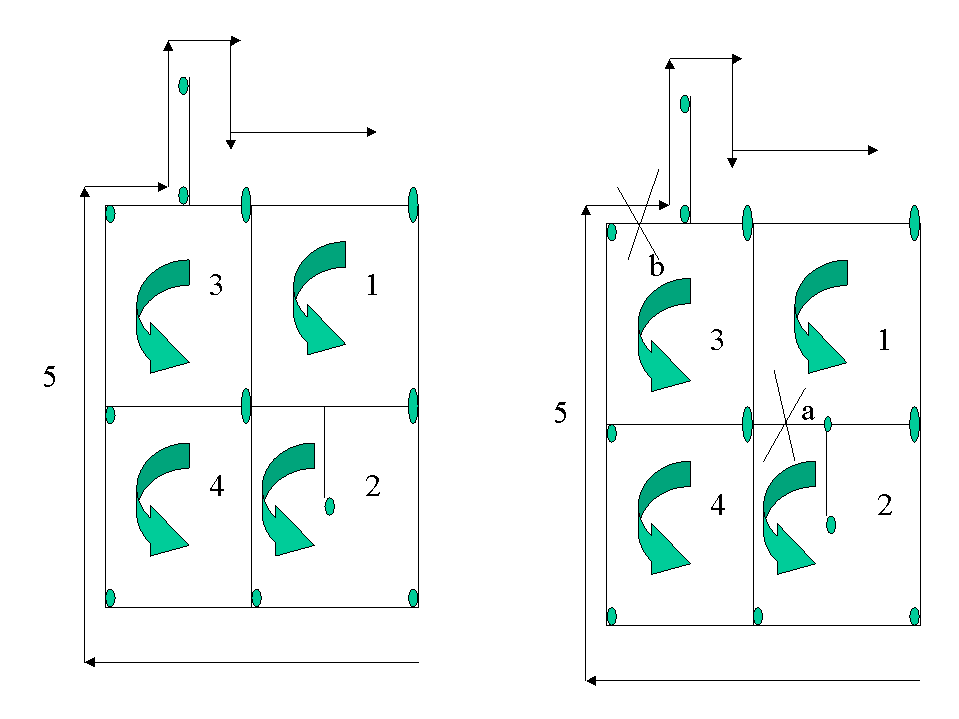
Figure 6: Protection Cycles
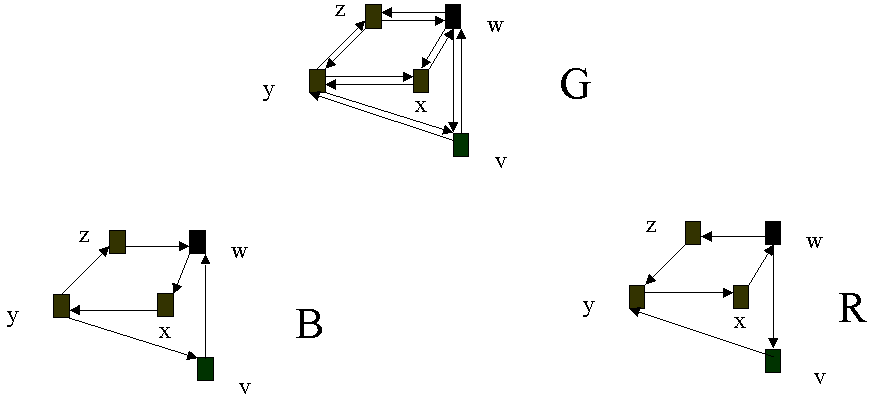
Figure 7. Illustration of WDM loop back using graph G (B and R are subgraphs of G)
Figure 8. A mesh connection of optical routers
Figure 9. FIS traveling along Reverse Notification Tree
Figure 10: Priority based optical layer switching
Table 1. Comparing point-to-point and ring architectures
|
1+1 Path Protection |
When applied to a ring, called as UPSR Bandwidth inefficient Requires diverse paths in the network Easy implementation Very costly, as separate bridges required for each path Useful in hubbed network implementations |
|
1:1 Line protection |
When applied to a ring, called as BLSR Can be done at a channel level (Called as BWLSR) More Bandwidth Efficient Low priority traffic supported Signaling required to the sender that the link has failed. More useful in rings |