Figure 1 - Hetereogenous Mobile Device MapReduce System
[Elespuru09]
Mitchell Shanklin, mds3@cec.wustl.edu (A survey paper written under the guidance of Prof. Raj Jain)
Cloud computing is the trend in which resources are provided to a local client on an on-demand basis, usually by means of the internet. Mobile cloud computing (MCC) is simply cloud computing in which at least some of the devices involved are mobile. This paper goes over multiple techniques and methods for mobile cloud computing. It explores both general-purpose mobile cloud computing solutions and application-specific solutions. It also discusses instances of mobile cloud computing where mobile devices serve as the cloud rather than the client. Finally it discusses some issues raised by this technology such as privacy and data ownership.
Keywords: "Cloud computing, Mobile cloud computing, smartphones, mobile applications
Cloud computing is defined as the trend in which resources are provided to a local client on an on-demand basis, usually by means of the internet.
One of the main benefits of cloud computing is reducing downtime and wasted expenditure for servers and other computer equipment. A given company is required to purchase the minimum amount of hardware necessary to handle the maximum points of stress on their system. Given situations where the strain and traffic are highly variable this leads to wasted money. For example, Amazon.com, a pioneer in cloud computing, at times used as little as 10% of their capacity so that they would have enough capacity to deal with those rarer high strain times [Robert06].
In the case of mobile cloud computing an additional significant benefit is brought to the table. Many mobile devices have significant constraints imposed upon them because of the importance and desirability of smaller sizes, lower weights, longer battery life and other features. This often severely constrains hardware and software development for these devices. Cloud computing allows devices to avoid these constraints by letting the more resource intensive tasks be performed on systems without these constraints and having the results sent to the device. Thus, cloud computing for mobile devices is a very appealing and potentially lucrative trend.
Several methods exist by which this trend can realize itself. First, methods have been proposed which aim to construct general systems for utilizing the cloud to help boost phone performance. This family of solutions can be referred to as general-purpose mobile cloud computing (GPMCC). Second, many individual applications used today with mobile devices such as smartphones employ cloud computing to a greater or lesser extent. There are multiple methods used and proposed by which the cloud can be leveraged. This can be referred to as application-specific cloud computing (ASMCC). Each of these two approaches has advantages and disadvantages and they are not mutually exclusive.
In addition to mobile cloud computing where mobile devices serve as the client and non-mobile devices serve as the server or mainframe, several papers have been written proposing an opposite model. In this model, mobile devices serve as the cloud that can be drawn upon. This paper will outline some work done in this area.
Finally, this paper will consider privacy and other concerns related to cloud computing, often specifically to MCC. These issues could cause a barrier to widespread use of mobile cloud computing and methods for resolving these issues could accelerate its adoption.
This paper makes a distinction between general-purpose (GPMCC) and application-specific MCC (ASMCC). Cloud computing is a very broad term and can feasibly apply to a wide variety of practices. All that is necessary to gain the label is for a mobile device to utilize the internet in order to use a specific resource in an on-demand manner. There are multiple individual applications which do that today. However, there is also the possibility of a more general-purpose use of these resources in order to help alleviate the limited computational power of mobile devices. It is feasible to develop systems in which tasks that are usually performed locally on the mobile device are outsourced to the cloud as they happen. This can leverage the computing resources of remote computers seamlessly without requiring applications specifically developed for that purpose. Specifically I will consider a proposed model in which this type of general-purpose cloud computing is done for smartphones.
Researchers from Berkeley have considered the possibility of increasing the performance of hardware-limited smartphones using cloud computing [Chun10]. Their main method involves creating virtual clones of smartphone execution environments on non-mobile computers and pushing task execution to these virtual devices. Because non-mobile devices often have significantly more computational power, this enables much better performance from smartphones. This could enable a broader spectrum of applications and could ease the burden of software developers to create ultra-efficient software for a more limited platform.
They describe five different types of augmentation they believe could be performed. First, there is primary functionality outsourcing. This takes intensive tasks like speech recognition or video indexing and ports them to the cloud while allowing less intensive tasks to still be executed on the phone itself. Second there is background augmentation. This type of augmentation takes tasks that do not need to be performed immediately, such as virus checking or indexing files and moves them to the cloud. Mainline augmentation allows users to specifically pick an application to be run in an augmented fashion. This preserves the workings of the program but changes the method by which it is executed. Hardware augmentation modifies the virtual clone of the smartphone to modify low level system software. For example, modifying garbage collection to be less aggressive (since less aggressiveness is needed on the clone which has more memory) can speed up execution significantly. Finally, augmentation through multiplicity uses multiple clones of the device to speed up execution. This can help applications which require a great deal of parallel processing.
GPMCC makes it possible to overcome the limits built into mobile devices, and is a promising aspect of MCC.
In contrast to GPMCC, application-specific MCC involves developing specific applications for mobile devices which use cloud computing. While both can potentially allow a mobile device to perform more intensive operations than it could using only local execution, ASMCC has the added benefit that it allows for uses of cloud computing which require more than simply increased computational power. For example, chat or e-mail clients require ASMCC because the internet is used as a communication resource and not simply for storage or additional computational power (although such applications may leverage these resources as well). Several methods and systems have been proposed which aim to specifically facilitate mobile cloud computing for applications. In this section we will cover them.
Researchers from Michigan State University have developed a system called Mobile Service Clouds. This system is designed to offer easy and automatic service configuration to create services which can be used by mobile consumers. Given that cloud computing relies heavily on the client-server model, a development like this makes it much easier to create services which can work with applications [Samimi06].
Jason Christensen has written about strategies for writing MCC applications using RESTful web services. RESTful web services (unlike standard web services) are easy to create, are not processor or time intensive, do not have continuous TCP connections and produce simple XML responses that can be easily parsed. Christensen claims that by leveraging mobile applications that use these services it will be more easily possible to create solid cloud applications [Christensen10].
Researchers from Pennsylvania State University have developed a system for elastic applications intended to be used on mobile devices. Their elastic application framework divides a full application into pieces called weblets. These weblets have the important feature of portability. Any given weblet can be switched between both mobile and stationary devices. One significant difficulty with this type of application is the requirement of security for these weblets, which they have a solution for. They believe that some aspects of their system could even be applied to other, non-mobile, cases of cloud computing [Zhang09].
These systems and methods outlined can help developers of MCC applications more easily leverage the resources of the cloud. Since specific cloud-leveraging applications provide many of the unique benefits of MCC these techniques will be of significant importance in the development of MCC.
So far in this paper, we have only discussed instances of MCC where the mobile device serves as a client and (assumedly) some collection of non-mobile devices act as the server, the provider of resources. It is possible to invert this pattern and let mobile devices serve as the resource rather than the consumer. We will call this mobile server cloud computing (MSCC). In this section we will consider a particular approach to this using MapReduce.
MapReduce is an algorithm which dissolves larger problems into smaller pieces that can be solved in parallel with multiple machines. Google created and publicized MapReduce. Given the large number of smart mobile devices connected to the internet, it seems possible to leverage these devices using MapReduce. The limited computational power of an individual device can be compensated for by the relatively small size of many of the tasks.
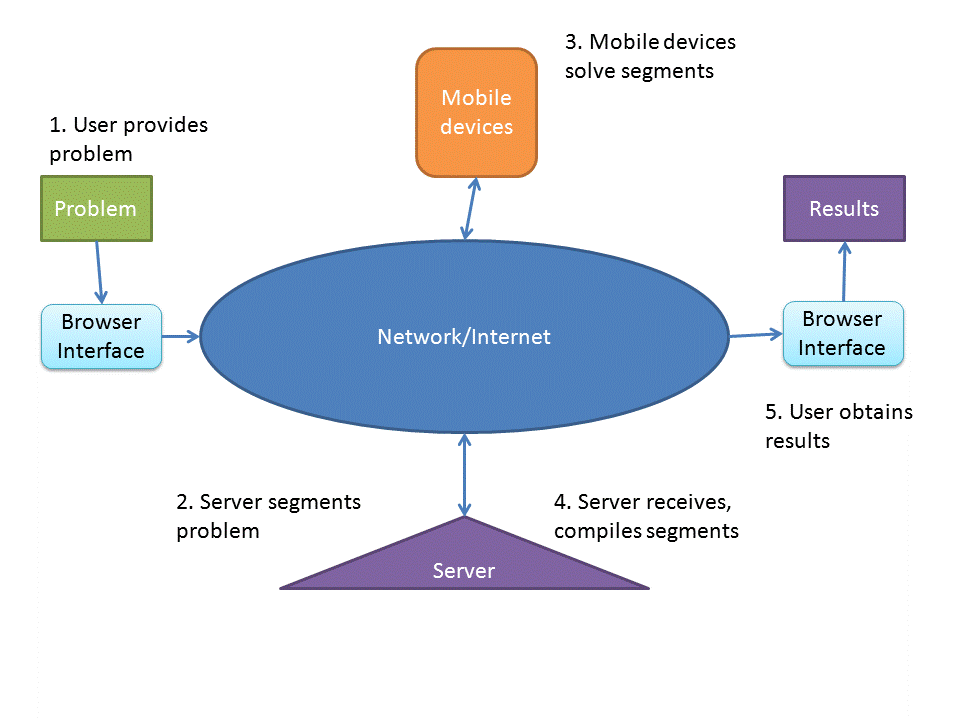
Researchers at the University of Colorado have considered this idea [Elespuru09]. They have created a system for leveraging mobile networked devices to solve problems. In designing this system they had to solve problems in several areas. First, they had to develop a system by which smartphone users could opt in to this program while staying aware of the effects. Second, they had to develop a system by which problems could be split over this device pool and the results could be aggregated. Finally, they had to make sure results could be transmitted to the requesting party and to make sure this could be done fairly quickly (difficult given the sometimes weak reliability of smartphones and their networks).

Figure 1 - Hetereogenous Mobile Device MapReduce System
[Elespuru09]
They developed a system consisting of several segments called the heterogeneous mobile device MapReduce system (see figure 1). First, they have a coordinating server which receieves problems, distributes them to nodes, aggregates results and returns the results. Second they have a client for a mobile device which receives, works on and transmits solutions to subproblems. Third, a browser interface which allows the user to submit problems and view results.
After performing tests they concluded that their system could indeed provide significant computational power if enough mobile users participated and recommended that this line of research be continued and possibly developed into a real world application. Thus, it seems likely that MCC is not limited to cases where mobile devices act as the clients.
Cloud computing as opposed to standard computing has several issues which can cause reluctance or fear in the user base. Some of these issues include concerns about privacy and data ownership and security. Some of these concerns are especially relevant to mobile devices. In this section, the paper discusses some of these issues, including both incidents involving them and techniques used to combat them.
One significant concern for cloud computing in general is privacy. For applications which employ cloud computing often at least some of the user’s data will be stored remotely. This leads to concerns that companies will use or sell this information as well as concerns that the information could be given to government agencies without the user’s permission or knowledge.
When it comes to mobile cloud computing, one family of applications specifically raises concerns. Location-aware applications and services perform tasks for users which require knowledge of the user’s location. Examples would include an application that finds nearby restaurants for the user or one which allows their friends and family to receive updates regarding their location [Cheng06].
This type of application simultaneously has broad appeal and brings significant concerns. One method sometimes used to alleviate concern is to make data submitted either spatially or temporally imprecise. This is called location cloaking [Cheng06]. The cost of location cloaking, of course, is that it can reduce the quality of service delivered by the applications. For example, if a user is attempting to find a nearby restaurant and the request sent to the server by his mobile client is too imprecise he could receive results which are irrelevant or perhaps miss relevant results. Thus, there is an interest in developing location cloaking methods which manage to alleviate privacy concerns and simultaneously reduce the negative effect on location-aware applications.
Researchers from the Hong Kong Polytechnic University have performed some useful work in this area, developing methods and policies for location cloaking which balance the factors discussed [Cheng06]. Specifically, they focus their attention on location-based range queries (LRQs), in which a mobile user makes a request for information regarding objects or points of interest within a certain range of their location. They propose a format for an imprecise location-based range query (ILRQ) in which both the location of the user and the location of the returned objects are ambiguous. In addition they present techniques used to prevent trajectory tracking: attempts to infer the future location of users given information about their past locations.
Another issue that arises from mobile cloud computing relates to the ownership of purchased digital media. With cloud computing it becomes possible to store purchased media files, such as audio, video or e-books remotely rather than locally. This can lead concerns regarding the true ownership of the data. If a user purchases media using a given service and the media itself is stored remotely there is a risk of losing access to the purchased media. The service used could go out of business, for example, or could deny access to the user for some other reason.
As shown by a recent incident, this concern can develop even when the media is not completely stored remotely. In July of 2009 Amazon remotely deleted and refunded copies of George Orwell’s 1984 from its users Kindle e-book readers [Stone09]. They did this because they discovered that 1984 was not actually in the public domain and that the publisher of that specific e-book edition of the novel did not have the right to sell or distribute it. This provoked an uproar among Kindle users and commentators. This action was compared to accidentally selling someone stolen property and then later breaking into their home to retrieve it.
This demonstrates that special precautions need to be taken with MCC to assure that incidents like this do not occur. Users should know exactly what rights they have regarding purchased media content. Either systems which imitate as closely as possible the normal processes of content ownership or systems which differ but communicate clearly the extent to which they differ should be used.
In addition to issues regarding privacy and data ownership there are the related issues of access and security. If an application relies on remote data storage and internet access in order to function at all then this can significantly affect the user. If, for example a user stores all of their calendar and contact information online, outages can affect their ability to function from day to day.
MCC is particularly vulnerable due to multiple points at which access can be interrupted. Reception and high speed availability can vary greatly for mobile devices. In addition to this, particular services used may have downtime. Finally, there can be issues of data becoming locked in to a particular service.
Concerns like the ones mentioned above have led some analysts to believe that MCC may be a trend which fails [Kharif09]. These concerns will definitely have to be considered and dealt with as MCC becomes more prominent.
MCC is a developing family of technologies that has the potential to vastly change the computing landscape. There are a variety of methods which are being used to further this trend which leverage the cloud in different ways. GPMCC has the potential to quite simply make mobile devices more powerful computing devices without altering their hardware, while ASMCC has the potential to both do that and to provide entirely new kinds of applications. While concerns and issues do trouble MCC, it is likely that many can be alleviated or countered. With luck, MCC will continue to expand and develop into a substantial and beneficial segment of the world’s computational activity.
URLs:
[Marinelli09] Marinelli, “Hyrax: Cloud Computing on Mobile Devices using MapReduce,”
http://www.contrib.andrew.cmu.edu/~emarinel/masters_thesis/emarinel_ms_thesis.pdf, September 2009.
[Chun10] Chun et al., “Augmented Smartphone Applications Through Clone Cloud Execution,” https://www.usenix.org/events/hotos09/tech/full_papers/chun/chun_html/, 2009.
Articles:
[Kharif09] Kharif, “Perils of the Mobile Cloud,” BusinessWeek Online, October, 2009.
[Stone09] Stone, “Amazon Erases Orwell Books From Kindle,” New York Times, July, 2009.
[Robert06] Robert, “Jeff Bezos' Risky Bet” BusinessWeek, November 2006.
Papers:
[Samimi06] Samimi et al., "Mobile Service Clouds: A Self-Managing Infrastructure for Autonomic Mobile Computing Services," Self-Managed Networks, Systems, and Services , 2006.
[Zhang09] Zhang et al., " Securing elastic applications on mobile devices for cloud computing," Proceedings of the 2009 ACM workshop on Cloud computing security, 2009.
[Elespuru09] Elespuru et al., “MapReduce System over Heterogeneous Mobile Devices,” Software Technologies for Embedded and Ubiquitous Systems, 2009.
[Christensen10] Christensen, “Using RESTful web-services and cloud computing to create next generation mobile applications,” Conference on Object Oriented Programming Systems Languages and Applications, March 2010.
[Cheng06] Cheng et al., “Preserving User Location Privacy in Mobile Data Management Infrastructures,“ Proc. of the 6th Workshop on Privacy Enhancing Technologies, 2006.
MCC - Mobile Cloud Computing
GPMCC - General-Purpose Mobile Cloud Computing
ASMCC - Application-Specific Mobile Cloud Computing
MSCC - Mobile Server Cloud Computing
LRQ - Location-Based Range Queries
ILRQ – Imprecise Location-Based Range Queries