| Azin Oujani, azinoujani@wustl.edu (A project report written under the guidance of Prof. Raj Jain) |
Download |
Anonymity has been requested for numerous purposes. The more sensitive information is transmitted through the Internet, the more people are concerned about their privacy. Therefore, anonymity systems and associated tools, which provide anonymity on the internet, are the central issue of this study.
This paper is organized as follows: First the difference between pseudonymity and anonymity, then anonymity systems and its components, and finally the two categories of anonymity system designs are being defined, in which it also introduces a few of the applicable tools in each design.
Pseudonymity with its Greek origin carries the "falsely named" meaning. It uses a pseudonym, a consistent disguised identity, which is linked to a single identifier keeping the real identity behind.
Publishing a public key is one of the simplest ways of deploying pseudonymity in which the confidentiality of the parties is provided, since the owner of the pair private key is the only one who can decrypt the message encoded. There are also Nym servers that use computer programs to give their users false identities as to post messages in newsgroups or send emails and have instructions on how to return messages to their real user.
Anonymity is also another Greek origin word meaning "name-less" which in turn is used where there is no identifiable information for an object or a person. The main difference between anonymity and pseudonymity is in anonymity the identity is unknown, whereas pseudonymity exploits the advantage of being unknown by using a pen name identity.
Anonymity receiver: No observer can identify the intended recipients of a message if the recipients are part of anonymity receiver set. Passive observers cannot identify other employers if the employee is to send a message to multiple employers that are included in anonymity receiver set.
Anonymity communication: Sender-Receiver anonymity is called anonymity communication, which makes the originator and recipient or even the whole communication unidentifiable from any observer. The employee and the employer are in the anonymity set, and any passive observer cannot identify the communication between them.
Anonymous communication design can be categorized into two general classifications: high-latency anonymity systems and low-latency anonymity systems. Before plunging into protocols and tools that offer Internet anonymity, it would be helpful to define the basic elements of most of the anonymous communications.
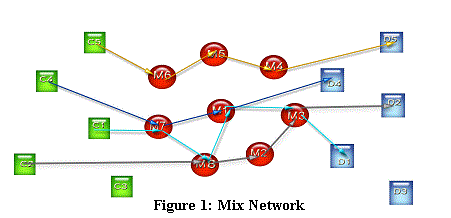
Illustrating the protocol, first client specifies destination of a message and selects an order of mixes. Then encryption algorithm proceeds in reverse order of the client’s path, and encrypts the message with the public key of the next hop in the mix. At last, each mix sends the message and detaches an encryption layer.
One of the most debated questions in the process of mix networks is the way to select the appropriate order of mixes. At the heart of much of the debate are mix cascade and free route. Both topologies are asymmetric while mix cascade is system defined and free route is user defined.
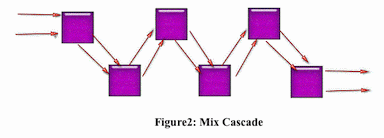
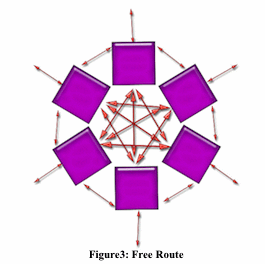
Threshold Mix: In this very simple algorithm, the messages will be forwarded in a random order to their next destination if the input of mix, cipher-text as mentioned above reaches to n packets, which n is defined by the mix. This is the original mix defined by Chaum, and is vulnerable to flooding attack.
Timed Mix: In this algorithm, the message will be forwarded in a random order to their next destination after t second which t is defined by the mix. This algorithm is vulnerable to the trickle attack.
Threshold Mix or Timed Mix: In this mixture algorithm message will be forwarded to their next destination, if either mix has received n packets or t seconds have passed. After sending the message mix resets the timer. This algorithm is vulnerable to blending attack, which is a combination of flooding and trickle attack.
Threshold and Timed Mix: Correspondingly, this combined algorithm will forward the message if t seconds have elapsed and mix has received at least n packets. Similar to previous algorithm, this one is also vulnerable to blending attack.
Threshold Pool Mix: In this algorithm after mix receives n packets other than f packets, which has been remained in the pool, it will randomly choose n packets, and forwards them to their next destination.
Timed Pool Mix: Similarly in this algorithm, mix collects packets after t seconds then adds them to f packets, which has been remained in the pool, and then randomly chooses n-f packets and sends them to their next destination.
Timed Dynamic Pool Mix: In this algorithm mix will randomly choose a fraction of whole messages in the pool, and forward it after t seconds have been elapsed. Pool mixes are vulnerable to blending attack.
Knowing these fundamentals will help to better understand the tools that provide high-latency anonymity systems.
This tool is not strong since it uses PGP 2 for cryptography, and does not add random padding to messages for each hop. Anonymous replies could be supported in this type of remailers via reply blocks. Type I remailers are still in use.
This protocol uses dynamic pool flushing algorithm, and SMTP for transport messages. In contrast to Type I remailers, anonymous replies are not supported in Type II remailer.
It uses TLS for forwarding messages. Additionally, in order to overcome anonymous reply problem, mixminion uses Single Use Reply Block (SURB) to secure reply messages as much as forward messages.
In contrary to high latency anonymity, low-latency anonymity systems are proxy based, which make them applicable for interactive or real-time applications. Accordingly some have called low-latency anonymity systems as connection-based system.
Lots of tools have been developed, on account of significant operation of low-latency anonymity systems on the Internet such as anonymizer.com, PipeNet, Tarzan, crowds, Java Anonymous Proxy (JAP), Morphmix, and so on.
The following part introduces the technique and a piece of software which employs that technique, most commonly in use for anonymous communication: Onion Routing and Tor.
Each server, which is called onion server, has a pair of public and private key, which the client gets to know the public key. Concentration of this proxy is to conceal the source and the destination of packets, although the message is encrypted with public key cryptography before transmission.
At first, a client selects a route to its desirable server, and then in a multi-layered model, encrypts its route with the public key of each node, in such a way that each node just knows the identity of its neighbor, and the interior layer contains the clear text message. Onion routing is not a two-way connection; however, reply onion, which is being sent all along with the message, makes it possible to respond to the client by setting up a reverse route.
Onion routed communications are at the risk of timing attack.
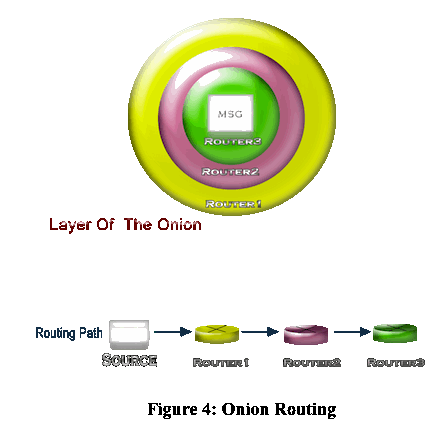
First, Tor establishes a circuit between the client and its destination by choosing a path of Tor nodes. Like Onion routing each node knows nothing about the path but the identity of its neighbors. The process of setting up a circuit is iterative, and is repeated around every 10 minutes in order to avoid traffic association to a specific user.
Given the description above, Onion routing techniques and inherently Tor; are limited in terms of area they cover to deliver the traffic as the final destination of the traffic is not part of the Onion network and needs the information to be delivered unencrypted.
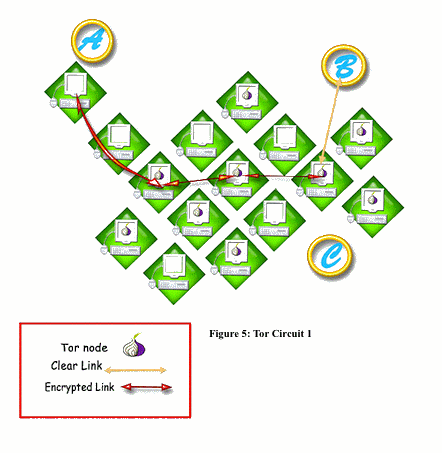
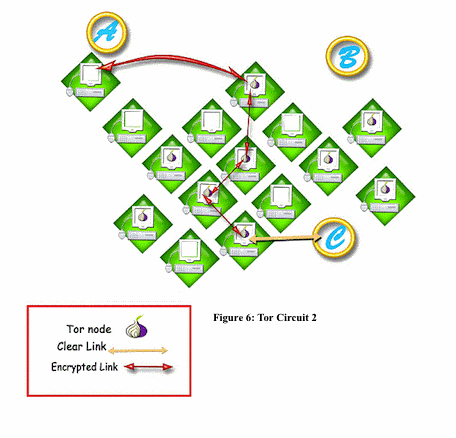
Based on the application for anonymity communication, whether it is delay sensitive traffic or any type of file transfer not sensitive to delay and latency; choosing a proper tool to deploy anonymity is very important. A proper tool will then take use of the most appropriate technique and protocol so that the required security and performance is achieved.
As there are multiple techniques and tools to deploy anonymity, I have tried to address some of the most common ways and explained how they tend to differ from each other. There are different strength and weaknesses for all techniques and tools addressed in the context of this report as any other security technology, by the main concern is how practical a technique or tool can be. Tor as one of the very popular means of anonymity has been around for a period of time now and it seems to be responsive as of yet.