Jianli Pan (jp10@cse.wustl.edu)
To implement Cafecrack idea under Windows XP, instead of using Untangle which is under a dedicated version of Linux, we use Wingate as the gateway software. Since it is not a free software, we could get a trial version for 30 days. We also use Apache 2.2 and PHP 5 to set up the phishing site. For the hardware, we need a laptop installed with the gateway software and a wireless AP or a wireless card running under AP mode in Linux. In short, we list the software and hardware needed in our implementation:
Hardware:
1. A Laptop with two Ethernet Interface (one for external link, another for internal link)
2. An AP(wireless router could also run under AP mode)
3. Maybe a USB to Ethernet transformation card since generally there is only one ethernet port in laptop. In fact we could also use wireless card as the external interface.
Software:
1.Wingate
2.Apache 2.2 for windows
3.Php5 for windows
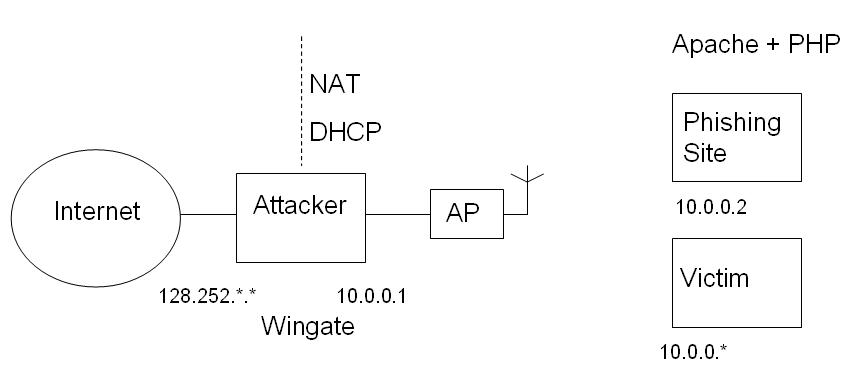
Our implementation is based on the following network structure:

1.Connect the network as the figure shown
2.Install Wingate on the Attack machine, and confige the ethernet interface connected to the Internet as External Link, and the ethernet interface connected to inside as Internet Link.
3.Configure "DHCP" function in Wingate. Here we set the internal link interface with the address of 10.0.0.1 and DHCP addresses range from 10.0.0.2 to 10.0.0.254.
4.Configure "DNS/WINS Resolver" function. Check the box "Lookup names in the system HOSTS file", and Click "Edit" to edit this file. In this file, add a line "10.0.0.2 www.gmail.com", in which the IP address is the address of the phishing site installed with our fake website and the password recording program.
5.Configure the Wireless Router working in AP mode, and using the SSID of "Free Internet Access", which will be seen by the victim.
6.Install Apache and PHP on the phishing site, and copy the recording php scripts and the fake webpage into the directory of Apache. Actually there are a lot of tutorials on how to install Apache and Php to work together in window and how to configure them. You can search for them by Google.
Basically, the attack machine will broadcast the SSID of "Free Internet Access"to the public without any encryption mechanism enabled. So careless user may not notice it and access it. Everything is normal by now, and all the traffic will pass the attack machine and be forwarded to the Internet. The attackers could sniff anything interested.
Now the user may type the URL of "www.gmail.com" in browser to access his mailbox. Since we have already configured to intercept this DNS request in the wingate in the HOSTs file, this DNS request will not be forwarded to the outside DNS server, it will be directly mapped into the IP address we designate in the HOSTS file. Here, we configure it to the IP address of the phishing site: 10.0.0.2.
The HTTP request for "www.gmail.com" now is forwarded to our phishing site and a preconfigured fake gmail webpage will be returned to the user. After the user input his account and the password and click the "log in" button. The account and password information will be stored in the phishing site because we insert some script into the fake webpage. After that, we will redirect the user to the real gmail login page. The real gmail page probably will return error information. Since this time, all the transaction will be between the real gmail website and the user, the user may not notice the error information, because he/she may think he/she has made a little typing mistake.